
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.
86-0769-39020536
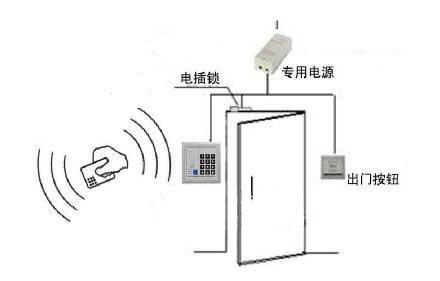 The access controller is the hardware core of the access control system, and its quality and performance directly affect the stability of the entire access control system. As the core data processing and storage part of the access control system, the access controller bears the card reading rights and access permission of the set card, monitors the entrance and exit status, records the access control events, and links with other systems such as alarm and fire fighting systems. The important function. With the in-depth development of access control technology, the future development of access control technology continues to improve.
The access controller is the hardware core of the access control system, and its quality and performance directly affect the stability of the entire access control system. As the core data processing and storage part of the access control system, the access controller bears the card reading rights and access permission of the set card, monitors the entrance and exit status, records the access control events, and links with other systems such as alarm and fire fighting systems. The important function. With the in-depth development of access control technology, the future development of access control technology continues to improve. March 08, 2024
Gửi email cho nhà cung cấp này
March 08, 2024

Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.

Fill in more information so that we can get in touch with you faster
Privacy statement: Your privacy is very important to Us. Our company promises not to disclose your personal information to any external company with out your explicit permission.